The Password Pandemic: A password “classification scheme” for the home or small business user
Humanity has a massive password problem. We might call it The Password Pandemic. Computers keep getting faster and cheaper, making passwords easier to crack, while human operators do not change their bad password habits. This is a losing proposition, with the advantage clearly toward hackers and cyber criminals.
Most users of the Internet now know that they need to use “strong” passwords, and that they should use a different password for each site. With a dozen or several dozen online accounts, this quickly becomes unmanageable. Exasperated, people just use the same (usually weak) password across several accounts. Hackers know this, and take full advantage. This is why “password dumps” are so useful to cyber criminals.
You have probably seen or heard of terms such as “Unclassified”, “Secret”, and “Top Secret” on TV. These data classification schemes basically describe how much time, effort, and money will be put toward protecting a particular type of data. To make an analogy, the formula for Coca Cola or the location of Jimmy Hoffa would be “Top Secret”, but the text of the Constitution of the United States would be “Unclassified”. We do very little to protect Unclassified information, but go to a great deal of trouble (and expense) to protect Top Secret information. This way, we can do the best job possible of protecting information, while keeping costs under control.
In a similar vein, some personal passwords are far more important than others. We may not care if our password to order from Pizza Hut gets stolen, but we certainly care if our banking and investments passwords get stolen. Conventional wisdom would suggest that we should definitely not use the same passwords for banking and pizza, but a person needs a system to follow.
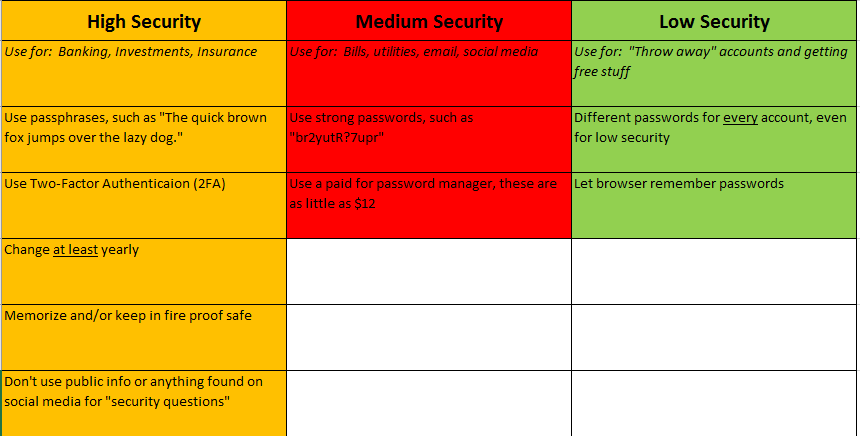
Divide your online accounts into three security categories – “Low”, “Medium”, and “High”. Which accounts go into which category is a personal decision, but here are some suggestions. Use a separate, dedicated email address for your High Security accounts (better yet, use a separate email address for each category).
- High Security accounts should include banking, investing, insurance, or anything relating to legal matters. You may also want to include health and medical accounts in this category (it’s up to you). High Security accounts are your personal “Top Secret” accounts, and you should manage their passwords accordingly.
- Medium Security accounts should include all of your bills and utilities, social media, App Store, email, etc. accounts. If you don’t place health and medical in High Security, put them in Medium Security. Again, it is a personal decision based on your own tolerance for risk.
- Low Security accounts are the junk accounts that we all create to get free stuff, order food, or get weather alerts (for example). We need to have a class of accounts that we don’t care about at all if they are compromised.
Password Classification
Now that we have “classified” our online personal accounts into Low, Medium, and High Security, we need have a way to create and manage these passwords. With current technology, it is more difficult to crack a passphrase than it is to crack a password. Remember that passwords (and passphrases) can usually have spaces in them – for example “The Quick Brown Fox Jumps Over The Lazy Dog” (Edit: please see the update about this passphrase at The Password Pandemic II: How To Create Awesome Passphrases) would be harder to crack (via brute force) than “br2yutR?7upR”.
Here is the weird thing about actual Classified Secret passwords used by the government – they are allowed to exist in two places; in a person’s head, and on paper. Yes, they are written down, but kept in specially sealed envelopes, inside of a heavy, expensive safe. Never allow any electronic device to save or store your personal High Security accounts. When available, use Two Factor Authentication (2FA) – an example of 2FA is when your bank texts you a single use code to use in conjunction with your passphrase. For these accounts, make sure that your “security answers” (for resetting your passwords) are never anything that is public information, or something that can be gleaned from social media.
Use a different passphrase for each account, memorize them and/or write them down, and keep them in the most secure location that is available to you – a fireproof safe is best. Ideally, only write down the passphrases themselves, with no other information. Change these passphrases at least annually. Since most people will only have a few accounts in the “High Security” category, this task should be overall very manageable.
Most of your online accounts will fall into the Medium Security category, and many people will have dozens of such accounts. For that reason, a paid for password manager (do not use a free one) is the best option available. A password manager will allow you to quickly and easily create complex and different passwords (passwords vs. passphrases are fine for Medium Security) for each and every account. This way, when one of your passwords is breached (which it will be), an attacker cannot use that password to try and log into your other accounts. It’s best to also change these passwords on a regular basis; how often is up to you. IMPORTANT — the password manager you choose will have a “master password”. This master password is definitely in the High Security category.
I don’t personally endorse one password manager over another, pcmag.com has a nice comparison chart for several of them here: https://www.pcmag.com/article2/0,2817,2407168,00.asp Steve Gibson, a highly respected security researcher, has in the past taken a liking to LastPass.
Lastly, are Low Security (throw-away) accounts. Many people will have dozens of these accounts as well. Create passwords for these accounts using an online random password generator, such the one at random.org: https://www.random.org/passwords/ Allow your browser to “remember” these passwords. This method is not considered to be very secure, but for our Low Security accounts, that should be fine.
This “personal password classification scheme” is not intended to be perfect – no security policy or procedure is. However, it is based on the best current practices available from the Department of Defense and other highly respected security frameworks. If you are an individual home or small business user with numerous online accounts, following this scheme will go a long way toward reducing your risk of becoming the victim of hackers or cyber criminals.
Please read our follow-up, “The Password Pandemic II: How to Create Awesome Passphrases” on how to create safer, more effective passwords.