Spectre Bug aka Spectre Attack – What You Need To Know
What is the Spectre bug aka Spectre attack?
Like the Meltdown bug, the Spectre bug is a hardware bug in the form of a CPU design flaw. Unlike the Meltdown bug which only affects Intel processors, the Spectre bug impacts Intel, AMD, and some ARM (used in many smart phones and other mobile devices) processors. These three are by far the most common CPUs on the planet, running literally billions of devices. In a Spectre attack, the CPU is tricked into executing instructions that it normally would not, causing leaks in the victims memory address space.
The entire Spectre white paper can be found here:
https://spectreattack.com/spectre.pdf
How bad is the Spectre bug?
Bad, due to the sheer number of affected devices, but still not as bad as Meltdown. Meltdown effectively breaks through all four rings of the CPU Protection Ring model, whereas Spectre is limited to the outer ring only.
In a Spectre attack, an attacker can (theoretically) force programs in the Application ring to arbitrarily read memory from other programs.
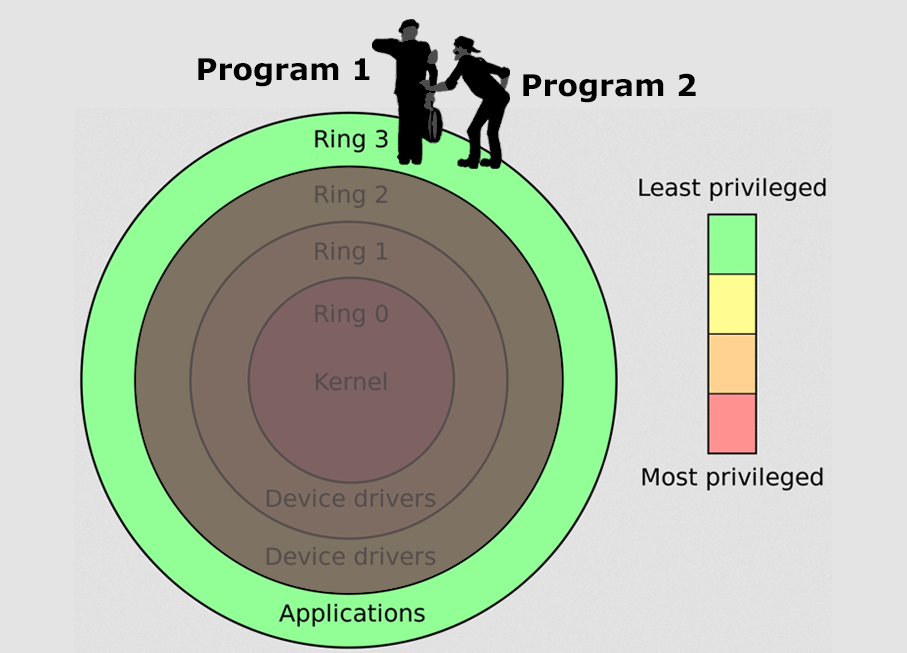
Spectre Attack
What should I do about the Spectre bug?
As of this writing, no mitigation (bug fixes) exists, so there is not much if anything that consumers CAN do, other than maintain situational awareness.
Is there any good news here?
Yes, definitely. A Spectre attack can only be executed in a lab by a gaggle of PhDs. Trying to pull this attack off would be like trying to stack Jenga blocks to a height of 25 feet on a crooked table as a drinking game. Possible, but very difficult. Even if an attacker could execute this attack, it is highly unlikely they would get anything of value out of it.
What about the bad news?
The bad news is that (like the Meltdown bug) the Spectre bug is a hardware flaw, but unlike Meltdown, there is no known way to defend against it, and a lot more research needs to be done. It’s at least possible that someone is going to come up with a way to do some bad stuff using this flaw. Just like when Rey handed Luke the light saber, we are stuck waiting for answers on this one.