Was YOUR company’s NIST assessment done properly?
Even though the deadline to be DFARS 7012/NIST 800-171 compliant passed over a year ago (December 31, 2017, to be exact), we at Stronghold Cyber Security have noticed a significant uptick in demand for these assessments. This is because the government has tasked the large prime contractors such as Northrup and Lockheed to ensure that their suppliers have complied, so these prime contractors are finally starting to crack down on their sub-contractors.
As I have pointed out many times in my presentations and here in this cyber security blog, cyber security practitioners are not licensed by the government like lawyers, accountants, or even hairdressers. Point being, there is no legal barrier to entry for selling cyber security services, and there are many companies offering these services who should not be or are doing poor work. Unfortunately, the burden is completely on the buyer to determine whether their chosen cyber partner is properly qualified or not. Legally speaking, Super Cuts could offer cyber security services if they wanted to, and there are no regulations or statutes (at this time) stating otherwise.
Recently, we began assisting a new client who previously had a NIST 800-171 assessment done by a well-known, “reputable” cyber security company. In order to help them we needed to review the assessment, which as it turned out was done haphazardly and is riddled with errors. What is worse, is that the client paid over $15,000 dollars for poor work that was done using an inexpensive automated tool, and by an obviously inexperienced person.
NIST 800-171 has 110 controls, but here we are going to talk about 3 of the controls that this NIST consultant answered incorrectly. I chose these ones because we found them within 10 minutes of reviewing the assessment. On our second pass, we found several more that were wrong. Not only that, the entire spreadsheet is filled with spelling errors that could be quickly corrected by a good-old F7.
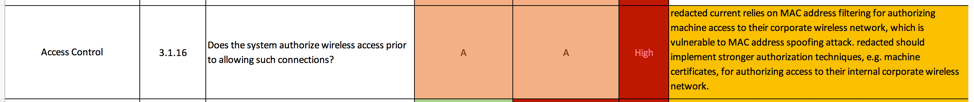
NIST 800-171 3.1.16 Access Control
The NIST 800-171 standard itself draws interpretation of this control from NIST 800-53 AC-18. The actual requirement reads:

NIST 800-53 AC-18
This customer is using Pre-Shared Key and Wi-Fi Protected Access 2 (WPA2). The actual requirement is to simply authorize wireless access, so simply by virtue of giving an employee the password, they are being authorized – as long as the process of giving the passwords out is controlled in some way.
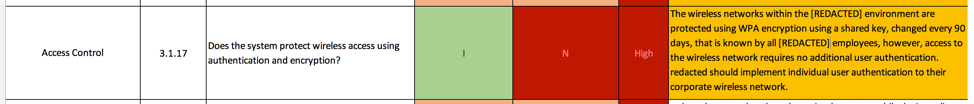
NIST 800-171 3.1.17 Access Control
Again, interpretation of this control from NIST 800-53 AC-18 and AC-18(1). The requirement is simply to have authentication and encryption in place. Again, this customer is using PSK and WPA2 – so the requirements of this control are actually met. In this case, MAC filtering would actually be a control enhancement. While it is true that RADIUS would be better than PSK, the standard does not require this in any way.
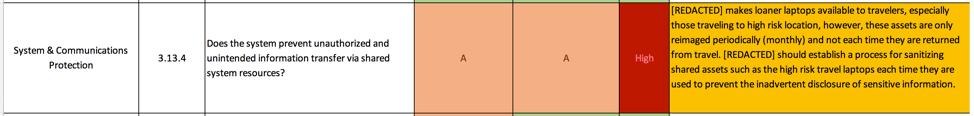
NIST 800-171 3.13.4 System & Communications Protection
This one is my favorite, because this answer for the NIST assessment isn’t even close. This control draws its guidance from NIST 800-53 SC-4. While the control text is confusing, what NIST is referring to by “shared system resources” are older file systems such as FAT16 or shared memory space; it does not apply at all to modern ring mode kernels, Address Space Layout Randomization (ALSR) or NTFS — the file system Microsoft uses. All three of these are common in today’s IT environment. Unless you have old hardware such as an AS400 or embedded controllers and the like, this control is almost always met.
Just as a CPA would prepare your taxes or a lawyer would prepare a will, a well-trained cyber security professional would easily avoid stupid mistakes like this. On top of the 15k already spent by the client, they are now needlessly spending more to get this cleaned up. Unfortunately, when it pertains to cyber security, at this time it is “Caveat emptor” – “Let the buyer beware.” Please make sure you properly vet any company before having a NIST assessment, or truthfully any cyber security offerings, done.