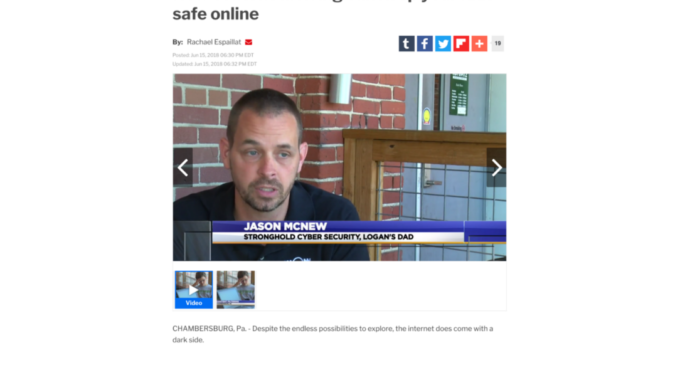
Stronghold Cyber Security CEO interviewed about content filtering for WDVM-TV
Jason McNew, CEO of Stronghold Cyber Security, discussed content filtering in a brief interview with Rachel Espaillat of WDVM-TV (formerly WHAG-TV) out of Hagerstown, Maryland on Friday, June 15. Jason appeared alongside his son Logan, as well as Barry Arendt…